May 7, 2023
Traffic Routing to Specific Microservices in AWS Using App Mesh
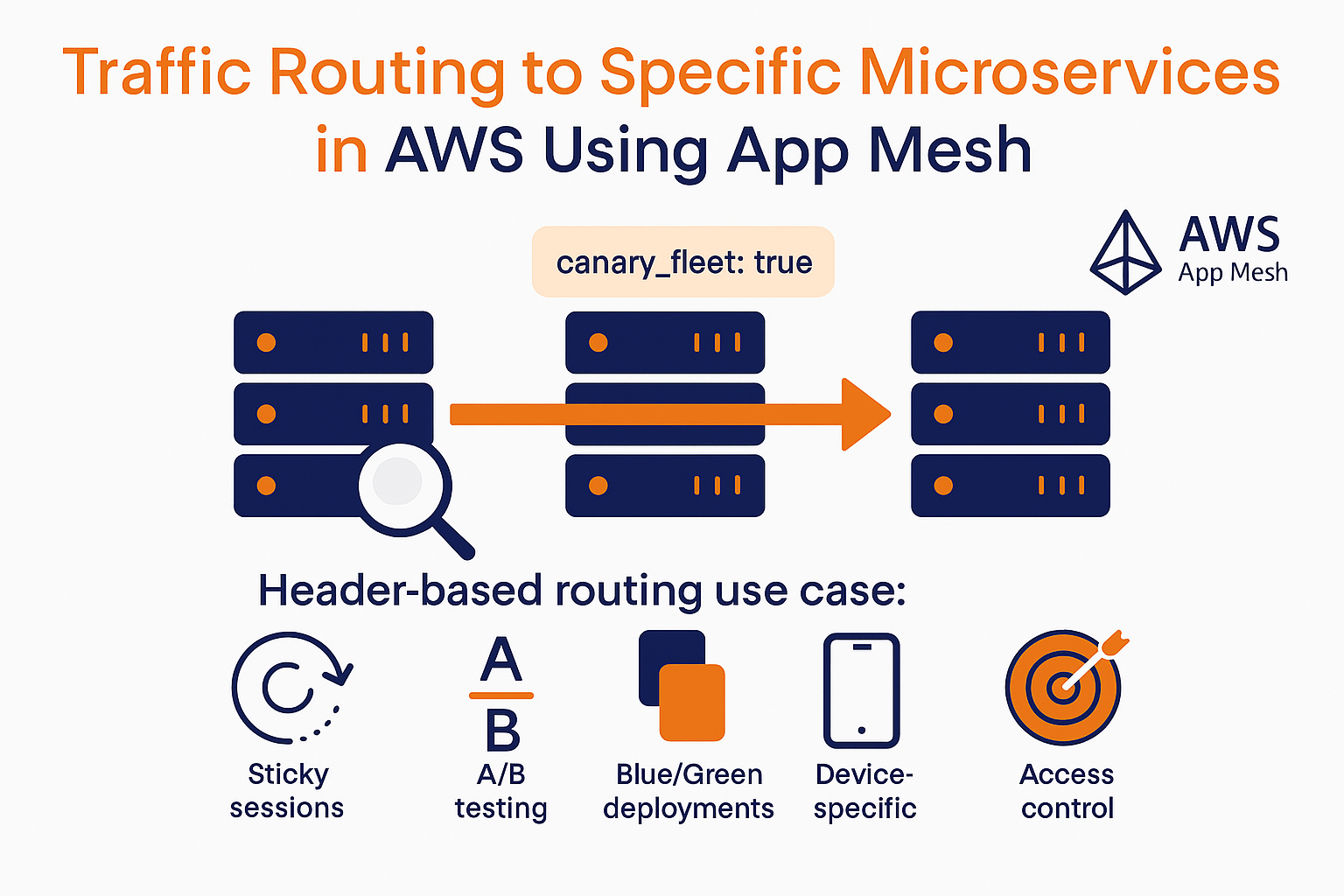
AWS App Mesh supports advanced traffic routing across microservices, including header-based routing. This method allows developers to route requests based on HTTP headers such as Accept, Cookie, or custom keys like canary_fleet.

Why Use Header-Based Routing?
Header-based routing helps support several use cases:
- Session persistence (sticky sessions)
- A/B testing via custom headers
- Canary or blue/green deployments
- Device-specific experiences (e.g., using regex on headers)
- Browser-based routing (e.g., using User-Agent)
- Access control based on IP or CDN (X-Forwarded-For)
Example: Route Canary Traffic Based on Header Value
In this example, we configure AWS App Mesh to route traffic only to the crystal-sd-epoch service if the request includes the header canary_fleet: true.
Create Traffic Routes
Instead of splitting traffic randomly across virtual nodes, the route directs traffic to the canary service only if the specified header is present.
# Define variables #
SPEC=$(cat <<-EOF
{
"httpRoute": {
"action": {
"weightedTargets": [
{
"virtualNode": "crystal-sd-epoch",
"weight": 1
}
]
},
"match": {
"prefix": "/",
"headers": [
{
"name": "canary_fleet",
"match": {
"exact": "true"
}
}
]
}
},
"priority": 1
}
EOF
); \
# Create app mesh route #
aws appmesh create-route \
--mesh-name appmesh-workshop \
--virtual-router-name crystal-router \
--route-name crystal-header-route \
--spec "$SPEC"Check Results
Use the following script to test if you’re consistently receiving responses from the canary service:
# Define variables #
URL=$(jq < cfn-output.json -r '.ExternalLoadBalancerDNS');
# Execute curl #
for ((i=1;i<=15;i++)); do
curl --location --silent --header "canary_fleet: true" $URL/json | jq ' .';
sleep 2s
doneBenefits and Challenges of Microservice Routing
As applications scale, managing service-to-service traffic manually becomes a bottleneck. With hundreds of microservices, developers struggle to locate errors, update traffic flows, and safely roll out changes.
A service mesh like AWS App Mesh simplifies this by handling:
- Service discovery
- Traffic routing
- Observability
- Security policies
- Deployment control
This reduces the need to hardcode logic into each service and enables a centralized control plane.
However, it introduces its own complexities—especially for operations. Monitoring, backups, API gateways, CI/CD pipelines, and security enforcement must all be well-configured to benefit fully from the mesh model.
Zero-trust networking is also a key practice. Just because two services can communicate doesn’t mean they should. Enforcing policies at the service level, backed by a centralized registry, is essential for maintaining security and order in a microservices architecture.

More News