November 25, 2022
How to Deploy AWS Web Application Firewall (WAF) in the AWS Cloud
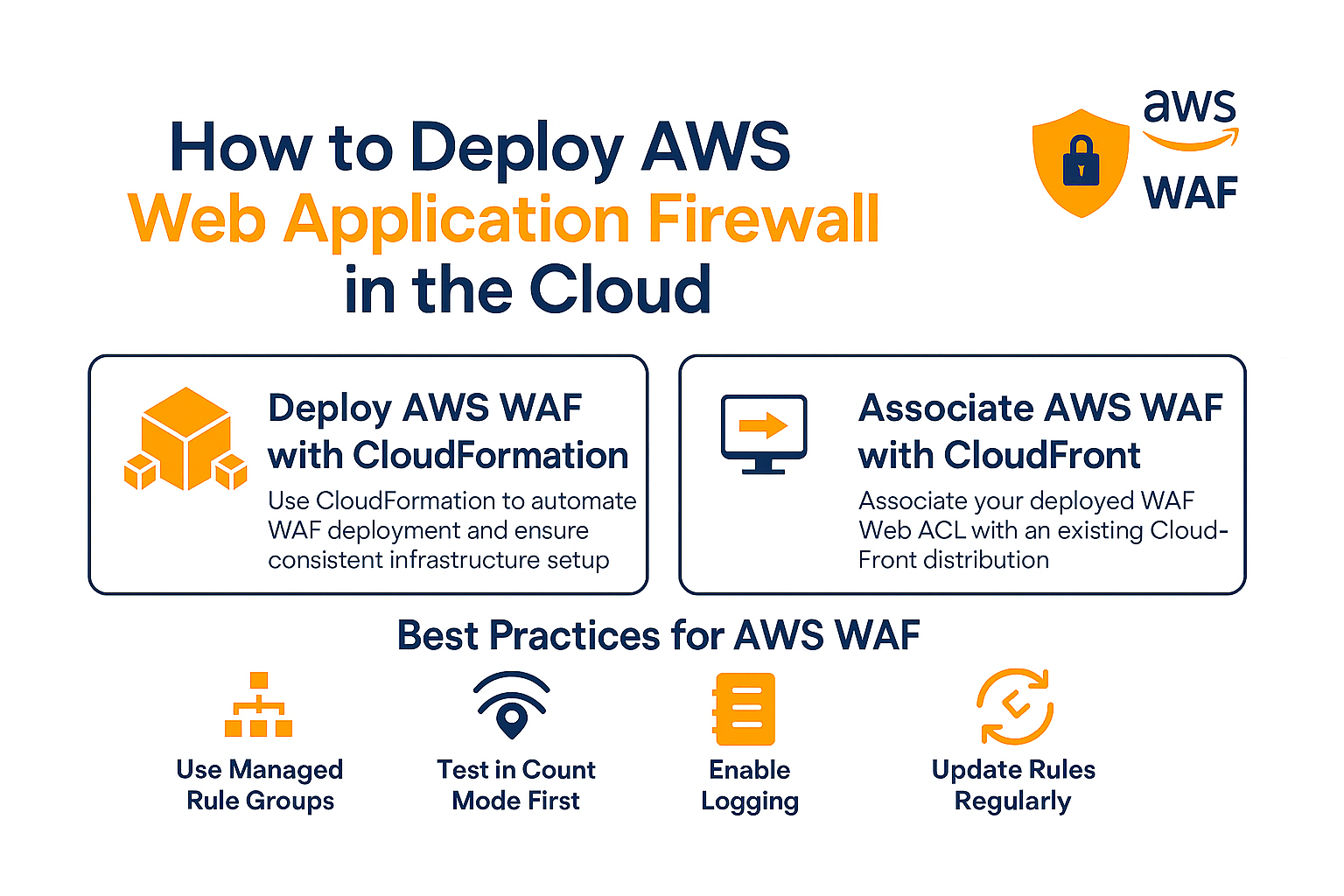
Protecting web applications from common exploits is critical. AWS Web Application Firewall (WAF) helps you monitor and filter HTTP and HTTPS requests to protect against attacks like SQL injection and cross-site scripting. This guide walks through how to deploy AWS WAF using CloudFormation and associate it with a CloudFront distribution.

Step 1: Deploy AWS WAF with CloudFormation
Use CloudFormation to automate WAF deployment and ensure consistent infrastructure setup.
- Open CloudFormation
Go to the CloudFormation console in your AWS account. - Start a New Stack
Create a new stack using either a template URL or by uploading your own template file. - Input Parameters
Enter required values such as the stack name, Web ACL name, and CloudWatch metric name. - Launch the Stack
Review all configurations, then launch the stack. Wait for it to finish creating the resources.
Step 2: Associate AWS WAF with CloudFront
After WAF is deployed, connect it to your CloudFront distribution to apply protection to your web traffic.
- Access CloudFront
Open the CloudFront console and start creating a new distribution. - Define Settings
Specify your origin and caching behavior. Under the Web ACL section, choose the WAF Web ACL you just created. - Deploy the Distribution
Finish the configuration and deploy the distribution. It may take a few minutes to go live.
Best Practices for AWS WAF
- Use Managed Rule Groups
Start with AWS Managed Rules to get baseline protection without having to create rules from scratch. - Test in Count Mode First
Apply rules in count mode to see what traffic they would block without actually enforcing them. This helps reduce false positives. - Enable Logging
Send logs to CloudWatch or an S3 bucket to monitor traffic and detect suspicious patterns over time. - Update Rules Regularly
Keep your WAF rules updated to defend against new types of attacks as they emerge.
By deploying WAF thoughtfully and following these practices, you can strengthen the security of your AWS-hosted web applications.

More News