August 6, 2022
SAML SSO for AWS: Updated Best Practices in 2025
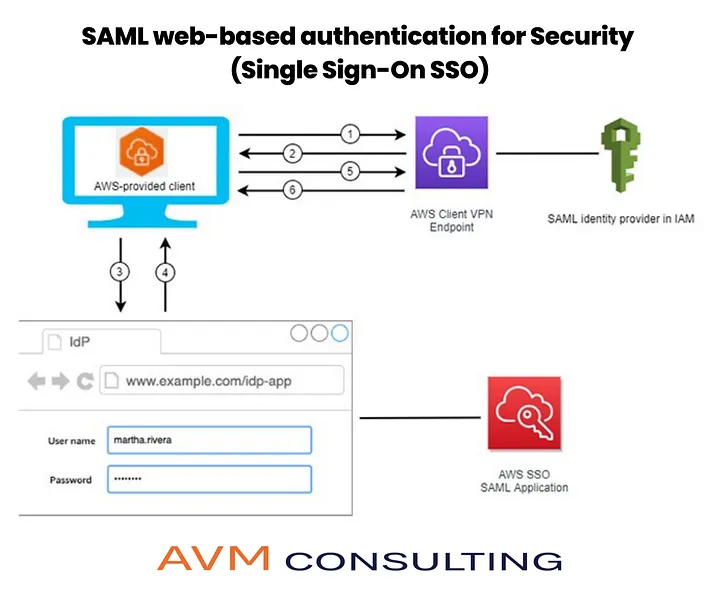
SAML 2.0 continues to be one of the most reliable ways to connect users from your identity provider to AWS without managing standalone AWS credentials. It enables users to log in with their existing enterprise credentials and gain access to the right AWS resources instantly.
But the way AWS supports SAML has evolved. If you’re still using the same configuration you set up in 2022, it’s worth reviewing your setup.
Key Changes in 2025
Encrypted Assertions Are Now Supported
AWS IAM now supports encrypted SAML assertions. That means authentication responses from your identity provider can be encrypted before being sent to AWS, reducing the risk of sensitive data being intercepted.
Expanded SAML Support in More Services
SAML authentication can now be used directly in more AWS services, including the OpenSearch Service UI. This gives teams direct access to tools and dashboards using their existing logins, with no need to manage additional access controls or service-specific credentials.
IAM Identity Center Is the New Standard
Formerly AWS SSO, IAM Identity Center is now the recommended way to manage SAML-based access to both AWS and external applications. It offers more flexibility, better UI, and simpler integration with services like Okta, Azure AD, and Google Workspace.
Improved Role Mapping and Session Control
You can now map user groups to IAM roles more granularly and manage session duration more precisely. This gives you tighter control over who can access what, and for how long.
What to Do Next
- Switch to IAM Identity Center
If you’re still using manual SAML integration through IAM, consider migrating to IAM Identity Center. It simplifies access control and scales better across multiple accounts. - Enable Assertion Encryption
Check whether your identity provider supports encryption. If it does, enable it for added security. - Review Your Role Mappings
Make sure user attributes in your SAML assertion align with IAM role requirements. Clean mappings prevent unexpected access issues. - Set Clear Session Limits
Limit session duration based on user role or access sensitivity. High-permission roles should have shorter session lengths. - Use CloudTrail for Auditing
Log all authentication activity using CloudTrail and set up alerts for unusual login behavior. This helps meet compliance requirements and adds visibility.
Summary
SAML SSO is still the go-to method for secure, centralized access to AWS. But the tooling and options have improved. If you’re managing user authentication in AWS, now is a good time to review your configuration and take advantage of the features added in the last few years. IAM Identity Center, encrypted assertions, and expanded service support make integration cleaner and security stronger.

More News







