May 3, 2023
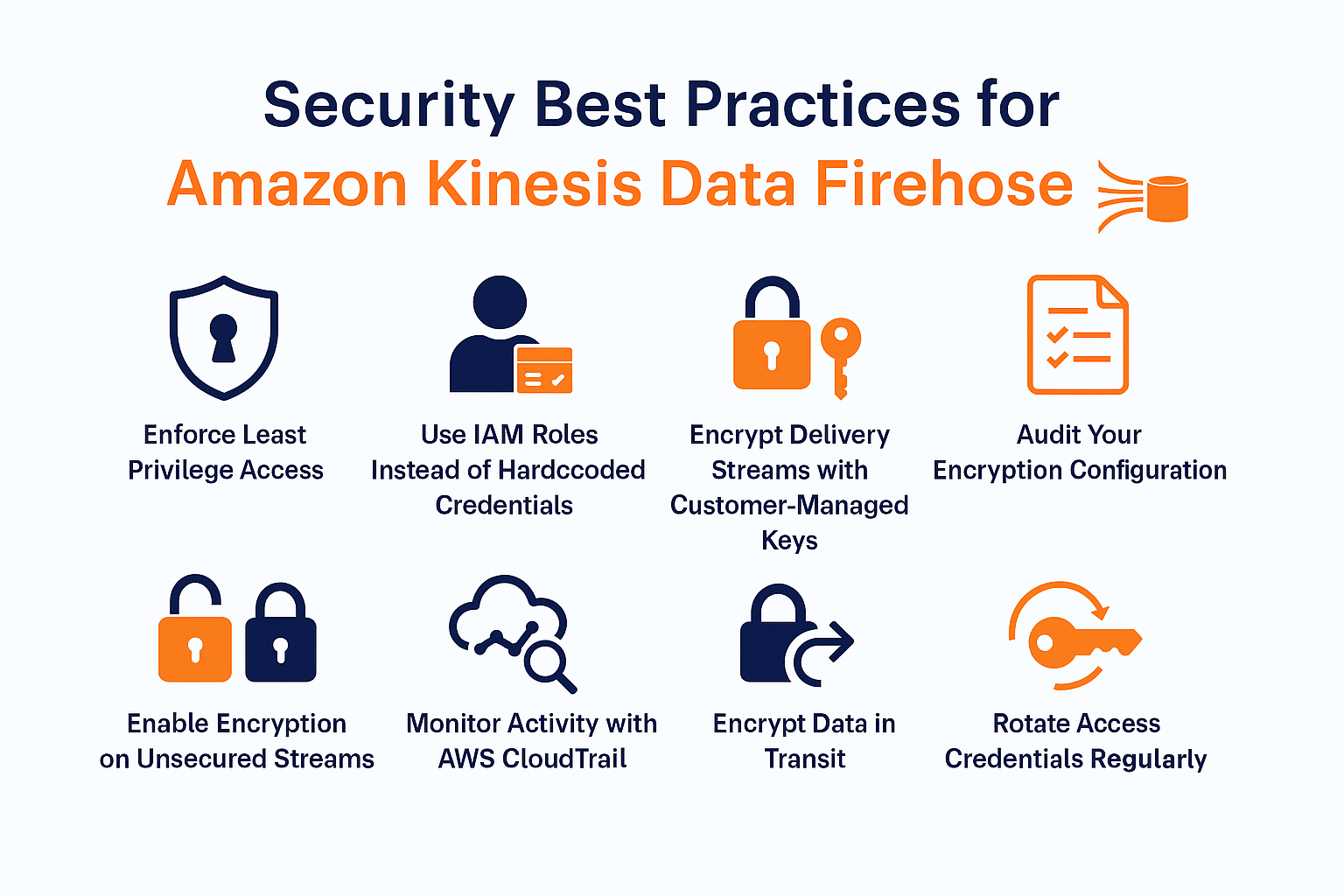
Security Best Practices for Amazon Kinesis Data Firehose
Securing your data streams is critical when working with Amazon Kinesis Data Firehose. Applying the right security measures ensures data confidentiality, integrity, and compliance with your organization’s policies. Below are key best practices for securing your Firehose delivery streams.

1. Enforce Least Privilege Access
Follow the principle of least privilege by granting only the minimum necessary permissions to users and applications. Use AWS IAM policies to define precise access scopes, limiting potential exposure.
2. Use IAM Roles Instead of Hardcoded Credentials
Never embed long-term credentials in your applications. Assign IAM roles to your producers and consumers, allowing them to use temporary security credentials automatically provided by AWS.
3. Encrypt Delivery Streams with Customer-Managed Keys
Use customer-managed CMKs to enable server-side encryption. While AWS-managed keys are available, customer-managed keys provide more control over policies, rotation, and auditing.
4. Audit Your Encryption Configuration
Periodically inspect your delivery streams to verify which encryption method is used. Ensure that all delivery streams are using server-side encryption and that key policies are up to date.
5. Enable Encryption on Unsecured Streams
If a delivery stream isn’t encrypted, update its configuration to use server-side encryption. Create a CMK, set the proper access controls, and apply it to the stream configuration.
6. Monitor Activity with AWS CloudTrail
Enable logging of API activity for Kinesis Data Firehose using CloudTrail. This gives you visibility into access patterns, helping you detect suspicious activity and troubleshoot permission issues.
7. Encrypt Data in Transit
Use TLS to encrypt data as it moves into Firehose. This prevents interception or tampering while the data is being transferred.
8. Rotate Access Credentials Regularly
Review and rotate access credentials on a regular basis. Doing so limits the window of exposure in case a key is ever compromised.
These practices help establish a secure foundation for working with Amazon Kinesis Data Firehose. Implementing them across your environments ensures that your streaming data remains protected end to end.

More News