November 27, 2023
QR Code Attacks: Risks & How to Protect Yourself
QR (Quick Response) codes have become an integral part of our daily activities, from making payments and accessing websites to contactless check-ins at venues. Amid the pandemic’s technological shifts, QR code usage soared, but so did associated risks. Cybercriminals exploit QR codes to steal data and perpetrate scams.
While QR codes offer significant convenience, they also present potential security threats. This article explores QR code attacks, their implications, and the countermeasures you can adopt to protect yourself and your data.
The Rising Popularity of QR Codes
QR codes have gained widespread popularity due to their versatility. They are used in various contexts:
- Payments: Mobile payment apps like PayPal and Venmo use QR codes for transactions.
- Login: Secure login through QR code features.
- Marketing: Marketers use QR codes on product packaging, flyers, and posters.
- Website Links: Quick access to websites or specific web pages via scanning.
- Event Ticketing: Electronic tickets for events such as concerts and conferences.
- Restaurant Menus: Contactless menu access in restaurants post-pandemic.
- Public Transport: Ticket validation and schedule information via QR codes.
- Inventory Management: Businesses track inventory with QR codes.
- Education: Teachers link students to resources using QR codes in educational materials.
- Healthcare: Hospitals use QR codes on patient wristbands for easy access to medical records.
- Authentication and Security: Two-factor authentication systems employ QR codes.
- Tourism and Travel: Travel guides use QR codes at landmarks for additional information.
These examples highlight the diverse applications of QR codes across industries.
QR Code Attacks: What You Need to Know
Despite their benefits, QR codes can be exploited by cybercriminals. Here are some common attacks:
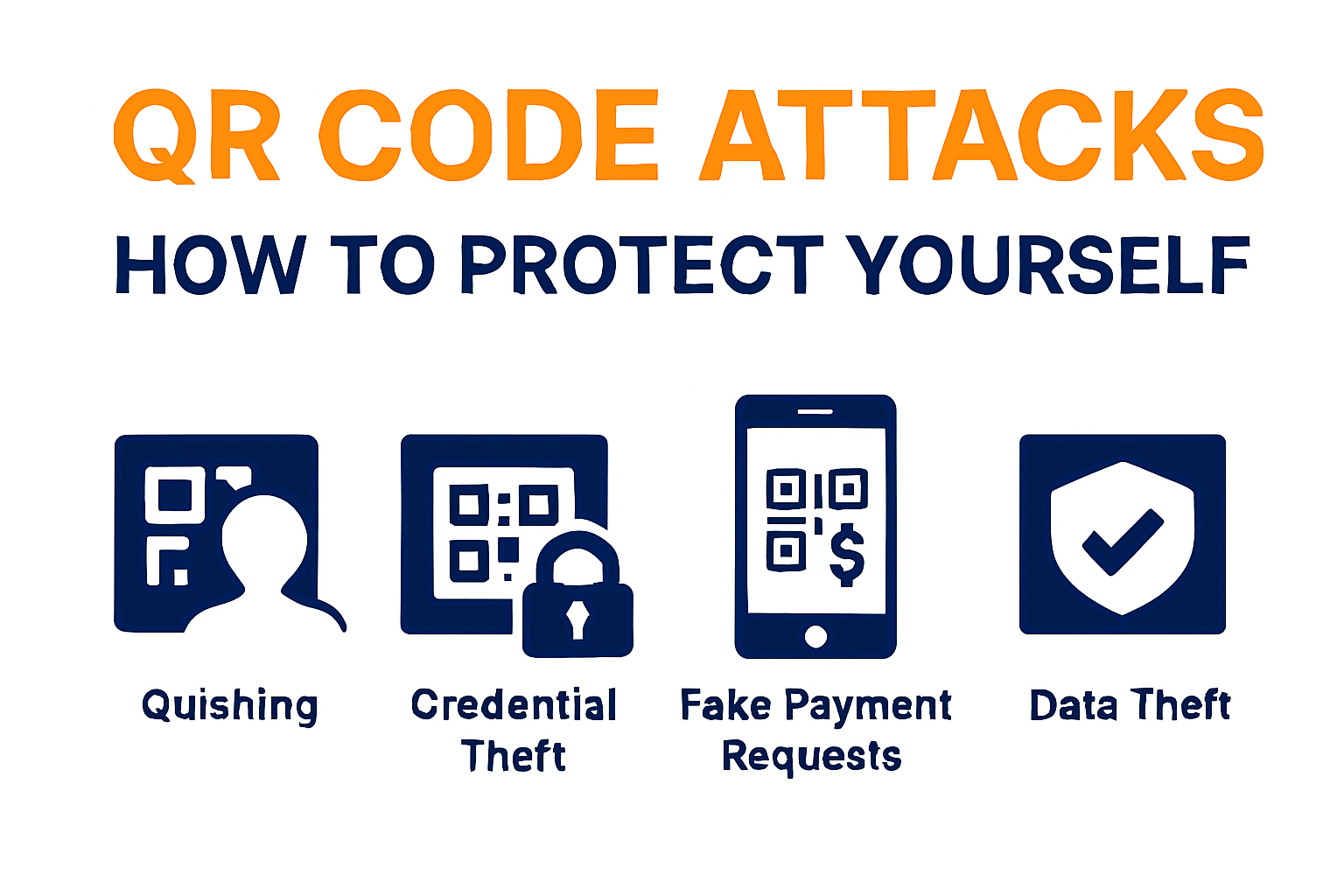
1. Quishing (Malicious URL Attacks)
Quishing involves sending phishing emails with harmful QR code attachments. Scanning these redirects users to fraudulent webpages designed to collect sensitive information like login credentials. The subtlety of this attack lies in its ability to bypass traditional email filters that scan for malicious links rather than images.
2. QRLjacking (Credential Theft)
QRLjacking exploits the Quick Response Code Login (QRL) system. Attackers trick users into scanning manipulated QR codes, compromising devices and granting attackers full control. This method is particularly dangerous as it can hijack entire sessions on platforms that utilize QR-based logins.
3. Fake Payment Requests
Scammers generate deceptive QR codes prompting users to make payments directly into fraudster accounts. These fake payment requests often mimic legitimate services, making it difficult for users to distinguish between authentic and fraudulent transactions.
4. Data Theft
Maliciously engineered QR codes can pilfer valuable data such as Wi-Fi access details or personal contact information when scanned. This type of attack can be particularly invasive, leading not only to immediate financial loss but also long-term privacy issues.
Furthermore, threat actors employ “honeypot” methods by offering free Wi-Fi networks capable of scanning QR Codes or substituting authentic public-area QR codes with deceptive ones directing users towards phishing sites.
Protecting Yourself from Potential Threats
To safeguard against these threats:
Verify the Source:
- Always verify the source before scanning any QR code; ensure it’s from a trusted sender or reputable company.
- Avoid scanning unknown or suspicious-looking QR codes found in public places without verifying their legitimacy.
Use Dedicated Scanner Apps:
- Employ dedicated QR code scanner apps equipped with additional security features like URL previews and safety checks.
- Opt for apps that offer real-time threat detection capabilities.
Exercise Caution Online:
- Exercise caution while sharing personal information online through websites accessed via QR codes; ensure the connection is secure by checking for a padlock symbol in the browser’s address bar.
- Be wary of entering sensitive information unless you are certain of the website’s authenticity.
Keep Systems Updated:
- Keep your operating system and software up-to-date to protect against known vulnerabilities that could be exploited by attackers.
- Regularly update antivirus software and enable automatic updates wherever possible.
Additionally, educating oneself about these risks can go a long way in staying vigilant while leveraging modern technology conveniences. Implementing these preventive measures can significantly minimize risks posed by malicious activities targeting both individual and enterprise users alike.
By following these best practices and staying informed about the latest threats, individuals can better protect themselves and their data from QR code-related risks. While QR codes offer convenience in accessing information, they also present opportunities for cybercriminals to exploit unsuspecting users.

More News